Navid Malek Personal Blog
This appliaction prototype was part of my project for E-Commerce course.
It was made with proto.io
There are other resouces for this application such as: Detailed Bussiness plan, Business model, App Workflow, etc.
Since they were available in persian, i didn't upload them on the Internet, but if anyone is interested in documents, just drop me an email!
How to run the prototype?
Just open index.html with a browser.
In this post we will learn how to proxy all the network's traffic (TCP and UDP) transparently through TOR with least difficulty.
Download full tutorial from here
Requirements:
-
Linux OS (tested on alpine and ubuntu)
-
iptables (Linux firewall)
-
RedSocks
What is RedSocks?
Reference: https://github.com/darkk/redsocks
Redsocks is the tool that allows you to proxify(redirect) network traffic through a SOCKS4, SOCKS5 or HTTPs proxy server. It works on the lowest level, the kernel level (iptables). The other possible way is to use application level proxy, when the proxy client is implemented in the same language as an application is written in. Redsocks operates on the lowest system level, that’s why all running application don’t even have an idea that network traffic is sent through a proxy server, as a result it is called a transparent proxy redirector.
System’s Architecture and Setup for TCP Connections
So this is the big image, almost every tcp packet will be redirected to port 12345 which redsocks service listens for incoming packets; after that, redsocks will redirect the received traffic to another ip and port in socks protocol format.

Also have in mind that for iptables in docker, you have to use docker run --privileged flag
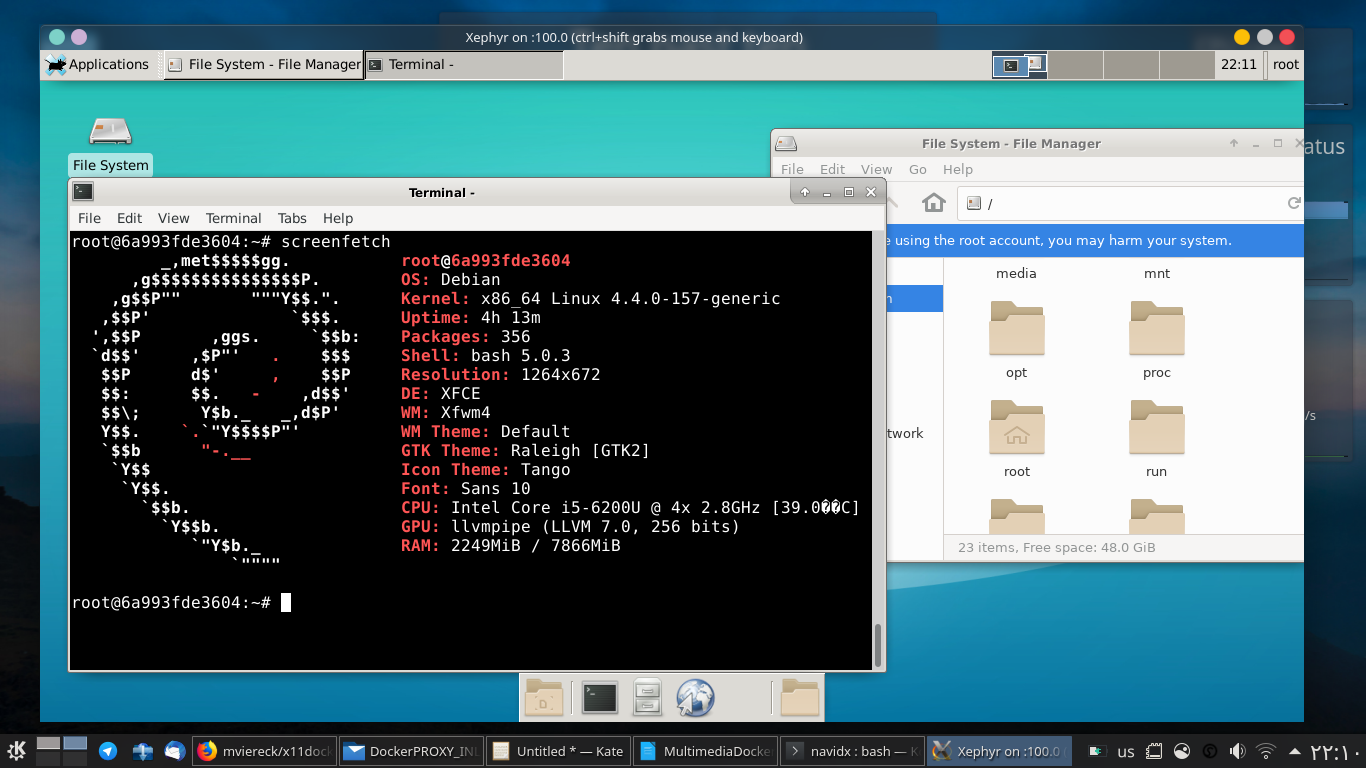
In this post I will show you not only how to run any multimedia application inside docker, but also in efficient and easy way.
Download full tutorial from here
Requirements:
-
Linux OS and Docker (tested on ubuntu)
-
X or Wayland (Linux Display Servers)
-
Ensure that the packages for an X or Wayland server are present on the Docker host. Please consult your distribution's documentation if you're not sure what to install. A display server does not need to be running ahead of time.
-
-
-
x11docker allows Docker-based applications to utilize X and/or Wayland on the host. Please follow the x11docker installation instructions and ensure that you have a working setup on the Docker host.
-
What is X11Docker?
Reference: https://github.com/mviereck/x11docker/
x11docker allows to run graphical applications (or entire desktops) in Docker Linux containers.
-
Docker allows to run applications in an isolated container environment. Containers need much less resources than virtual machines for similar tasks.
-
Docker does not provide a display server that would allow to run applications with a graphical user interface.
-
x11docker fills the gap. It runs an X display server on the host system and provides it to Docker containers.
-
Additionally x11docker does some security setup to enhance container isolation and to avoid X security leaks. This allows a sandbox environment that fairly well protects the host system from possibly malicious or buggy software.
Here are the slides from my presentation at Nopayar, when I used to be a DevOps Engineer.
The slide contains many best practices gathered (not written) by me for better scaling and high-availibility of applications. ( mainly web applications)
The slide covers:
- ScalingHierarchy
- Pinterest Best Practices
- Data Partitioning and Sharding Patterns
- Sharding Considerations and Techniques
- ProxySQLSharding and
- ID Generation Approaches
- Query Optimization
I've tried to put a refrence for each section for more information, but there are some sections that don't have any refrence at all, you can easily find the refrences with a quick search in Internet.
The main project that me and my colleague designed for Operating Systems course ( Spring 20 ) - TA of OS
Project Description ( summary ):
The goal of this project is to gather information about incoming and outgoing packets in system. ( some kind of packet capturing )
The desired informations are :
- Lenght of packet
- Protocols of packet ( in all available layers of network except application layer, for example Ethernet,IP,TCP )
- Hash value of packet
- Total Processing time of packet
Phase one :
- implement a systemcall with a single integer input indicating what information you desire from packets and single output buffer to copy the data from kernel space to user space.
- an interactive user space program that talks to the user and systemcall call above ( clean input and output for user ).
Phase two :- implement a kernel module with a single proc entry file for input indicating what information you desire from packets and single proc entry file for output and to copy the data from kernel space to user space.
- an interactive user space program that talks to the user and kernel module and proc entry files above ( clean input and output for user ).
Phase three :
Performance comparsion of kernel module and system call ( the first two phases ).
DOWNLOAD PROJECT DESCRIPTIONS IN DETAILApproach Taken for answer:
All of the desired informations are in sk_buff data structure.
my approach was to clone sk_buff from driver, right before the driver ( here : e1000 ) wants to pass the packet to the next network layer handler ( application or the NIC ). with this approach i will have a clone for each packet.
now that i have the information the rest is easy, just copy the desired information from the sk_buff to the output buffer and copy from there to user space.
- رویای بیت کوین Bitcoin Dream
- پرسش و پاسخ وردپرس
- سایت کیم کالا فروشگاه اینترنتی
- Lotus Water
- Psychology
- سایه وارونه
- داده پردازی نرم افکار
- اپیکیشن نت مانی net money
- مرکز تخصصی گچبری و قالبسازی آذین
- بیوگرافی
- ابوالفضل بابادی شوراب
- گروه هنری اولین اکشن سازان جوان
- اقیانوس طلایی
- .:: تنفّس صــــبح ::.
- شین نویسه
- خبر
- شهدای مدافع حرم
- پایکد
- نقاشی کشیدن
- درمان مو
- کبدچرب
- Sh.S
- نمونه سوالات استخدامی بانک تجارت (فروردین 1400)
- رسانه ارزهای دیجیتال و صرافی Coinex
- مرکز ماساژ در تهران
درباره این سایت